Software Development: A Solid Foundation for Software Development
Software Development Principles is one of the "standard" principles that can be applied to the program code we create. If we apply the SOLID principle, then the code we create will be much better; Easier to maintain, flexible, reusable, extendable. In other words, our code becomes more "pro".
SOLID popularized by Uncle Bob (Robert C. Martin), even though some of the items in it have been popularized before by others. Uncle Bob is the author of the book "Clean Code: A Handbook of Agile Software Craftsmanship”. This is one of the books that we recommend to every programmer to read.
“Writing clean code is what you must do in order to call yourself a professional. There is no reasonable excuse for doing anything less than your best.”
Robert C. Martin
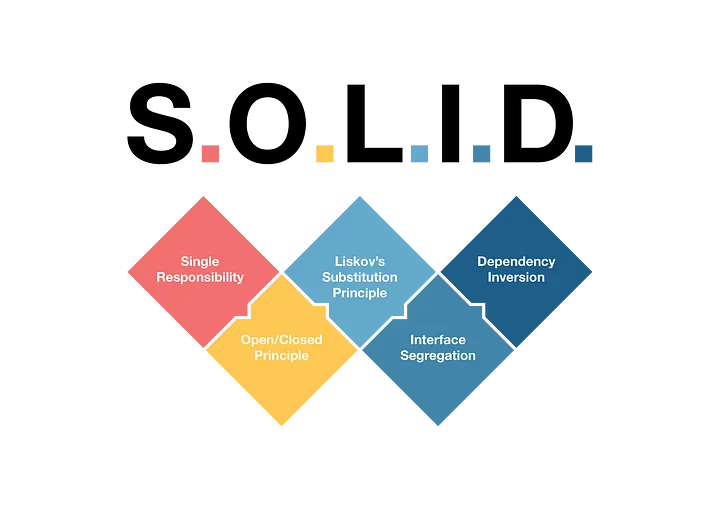
SRP (Single Responsibility Principle)
Definition: "A class should have one and only one reason to change (single responsibility)" In a class, only one responsibility can be filled. Don't put a variety of code into a single class. Example: If the class is responsible for managing the "users" table, then it should not be overloaded with the "orders" table for example, or by adding a year-end discount calculation. Discount calculations should be separated into separate classes. The management of the "orders" table must also be separated into separate classes.
Why is this important?
- When writing a class or function dedicated to a single function, it is easier to understand, maintain, and modify your code.
- If you want to change the functionality of the system, it will be easy to find the parts of the code that need to be changed.
- Make the code more organized and easy to read. It also makes code reuse easier.
OCP (Open Closed Principle)
Definition: "Entities (classes, modules, functions etc.) should be open for extension but closed for modifications". The class/function must be extendable without changing the code in it. Hmm sounds tricky, but in programming it can be done.
This idea is facilitated by the Open/Closed Principle. Our functions, classes, and modules should be designed in such a way that they are open to expansion, yet closed to modification.
- Open for Extension: New functions can be added to classes and modules without breaking existing code. Composition and heritage can be used to achieve this.
- Closed for Modification: We recommend that you don't make changes that break the current functionality, as this requires refactoring from existing code and writing some tests to make sure the changes work.
LSP (Liskov Substitution Principle)
Dedefinition: "Functions that use pointers or references to base classes must be able to use objects of derived classes without knowing it". Classes must be switchable with their child classes without causing logical or technical errors.
ISP (Interface Segregation Principle)
Clients should not be forced to depend upon interfaces that they do not use."
The interface is created according to the client's needs, and should not force the implementation of all functions. Because, maybe some functions are not needed by the class.
DIP (Dependency Inversion/Injention Principle)
Definition: "Clients should not be forced to depend upon interfaces that they do not use." A. "High level modules should not depend upon low level modules. both should depend upon abstractions." B. "Abstractions should not depend upon details. Details should depend upon abstractions."
Similar to SRP, but this applies to the interface. Interfaces should also not have too many functions that force the client class to implement all the functions. Because, maybe some functions are not needed by the class.
Conclusion
- Prinsip Single Responsibility (SRP) :
By separating responsibilities in different classes, we create code that is easier to understand, manage, and fix. Every class should have one reason to change.
- Prinsip Open/Closed (OCP) :
The code should be open for extension but closed to modification. This encourages the use of inheritance and polymorphism to change behavior without changing existing code.
- Prinsip Liskov Substitution (LSP) :
SubClass should be able to be used in place of the parent class without affecting the correctness of the program. This ensures semantic relationships between classes.
- Prinsip Interface Segregation (ISP) :
The interface that is specific to each class helps avoid unnecessary implementation. Classes should only implement what is necessary, preventing excessive influence.
- Prinsip Dependency Inversion (DIP) :
Relying on abstraction rather than concrete implementation allows for flexibility and avoids strong dependencies between system components.
PT Neuronworks Indonesia is present as a trusted partner in the implementation of reliable and scalable information technology solutions. With more than 10 years of experience in the IT industry, we are ready to help optimize your business database infrastructure with High Availability solutions that are customized as needed.
Hubungi Tim Ahli Kami Sekarang for a FREE consultation on the right issue for your business!





 Have any question?
Have any question?